Achieve Business Connection With Secure Cloud Storage Space Services
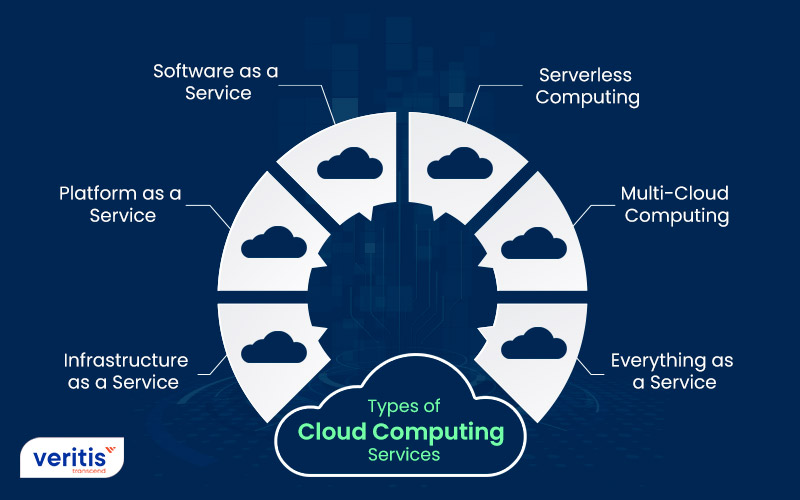
Advantages of Secure Cloud Storage Space
Undoubtedly, safe cloud storage uses businesses a wide range of advantages in regards to information protection and accessibility. Among the main advantages is improved security. By saving data on reputable cloud systems that employ file encryption and advanced protection steps, organizations can secure their details from unauthorized accessibility or cyber risks. Safe cloud storage space allows for seamless scalability, making it possible for businesses to quickly increase their storage space as needed without the headache of physical upgrades. This scalability is particularly useful for expanding businesses or those experiencing varying information storage space needs. Additionally, cloud storage promotes effective cooperation amongst team members, as it enables real-time access to shared papers and documents from anywhere with an internet link. This ease of access improves efficiency and improves workflows by eliminating the restraints of physical storage devices or location-dependent gain access to. On the whole, the benefits of secure cloud storage equate into enhanced data management, raised operational effectiveness, and improved security for businesses of all sizes.
Key Features for Service Continuity
By distributing information throughout different servers or information facilities, businesses can minimize the danger of information loss and guarantee continuous access to their information. Overall, these key attributes function together to form a comprehensive business connection method that safeguards important data and operations.
Importance of Information File Encryption
In today's interconnected digital landscape, safeguarding delicate information is extremely important, making the value of information encryption a basic element of maintaining data honesty and safety. Information file encryption entails encoding info in such a way that just licensed parties can access and understand it. By transforming data right into a secure layout, file encryption works as a shield versus unapproved access, reducing the threat of information breaches and cyber dangers.

Calamity Healing Techniques
A robust catastrophe healing plan includes detailing treatments to recuperate data, applications, and IT facilities in the event of a disaster. One essential aspect of an effective strategy is regular information back-ups. By keeping data in protected cloud storage solutions, organizations can make certain that essential details is shielded and quickly available in case of a disaster.
Picking the Right Provider
To make certain seamless service connection and effective disaster healing, picking a appropriate and reputable solution copyright for protected cloud storage is paramount. Guarantee they utilize durable file encryption approaches, have stringent gain access to controls, and conform with sector laws to safeguard your data. Additionally, evaluate the check supplier's information recuperation capabilities.
Additionally, think about the scalability and versatility of the cloud storage service. Your company requirements may progress gradually, so it's necessary to pick a provider that can accommodate your expanding storage space demands and adapt to altering situations. Examine the provider's track document and online reputation in the sector. Try to find evaluations, reviews, and study to determine their dependability and performance. By carefully reviewing these variables, you can choose a cloud storage solution supplier that aligns with your business's demands and makes sure continuous procedures when faced with potential disturbances.
Final Thought
In conclusion, safe cloud storage solutions offer crucial benefits for attaining company connection, including boosted safety functions, smooth scalability, reliable partnership devices, durable data backup systems, and calamity recovery methods. Information encryption plays a critical role in protecting delicate details, while choosing the best company is key to guaranteeing conformity with click for source laws and learn this here now keeping operational efficiency. cloud services press release. Safe and secure cloud storage space is a valuable asset in today's digital landscape for guaranteeing undisturbed organization procedures
Data backup systems are crucial for safeguarding against data loss due to system failures, cyber-attacks, or human errors. By distributing information throughout numerous web servers or information facilities, services can alleviate the danger of information loss and make sure constant access to their information.In today's interconnected digital landscape, safeguarding sensitive details is extremely important, making the relevance of information security an essential element of maintaining data honesty and protection. By transforming data into a secure layout, file encryption acts as a shield against unapproved gain access to, decreasing the risk of information violations and cyber risks.
Compliance needs and information protection regulations usually mandate the usage of file encryption to safeguard delicate info, emphasizing its essential function in modern information safety techniques.